Unit 4 law and order Reading(1):Fight against cybercrime.课件(34张)
文档属性
| 名称 | Unit 4 law and order Reading(1):Fight against cybercrime.课件(34张) |

|
|
| 格式 | zip | ||
| 文件大小 | 3.0MB | ||
| 资源类型 | 教案 | ||
| 版本资源 | 牛津译林版 | ||
| 科目 | 英语 | ||
| 更新时间 | 2019-08-04 00:00:00 | ||
图片预览











文档简介
课件34张PPT。Welcome
to
our class!By the end of the lesson, the students will be able to:know more about cybercrime
to master the reading skills of definition and skimming
to learn to summarize the text using the phrases learned in the text
12.9
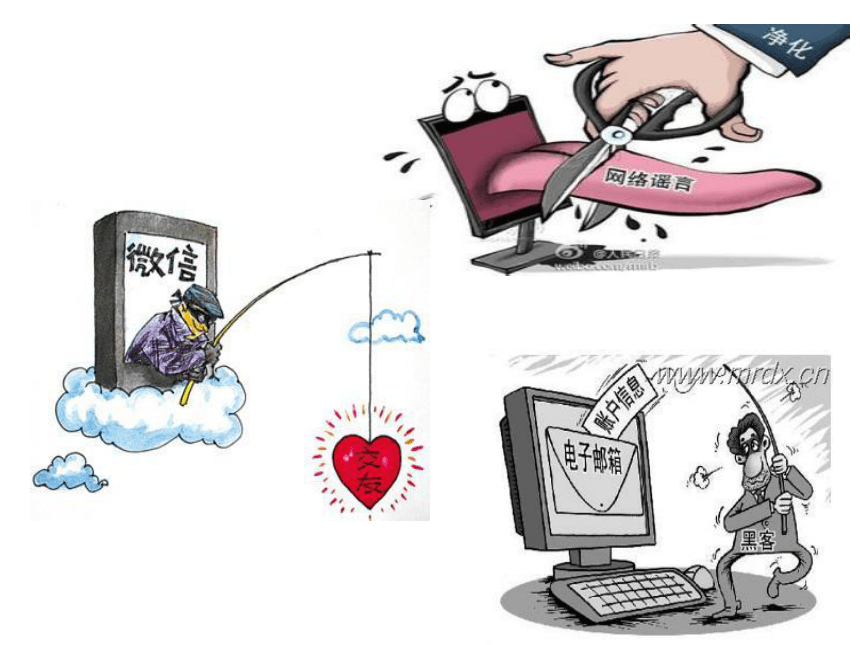
On 12.9,1935 people went on street to call for a revolution against Japan to improve our life.Now we're again experiencing a revolution which changes our life a lot*Edward Snowden revealed the top-secret documents about the USA's surveillance programme.(监听项目)*Suzhou news said that Mobile Power Pack(手机移动充电宝) can steal customers' information while people are charging their mobile phone.Do you think it's legal or illegal?
we call this criminal offence related to the internet cybercrime.Have you ever experienced or heard about more examples about cybercrime?Group work Reading---let's know more about cybercrime.The fight against cybercrimeFast reading1.How many categories of cybercrime are listed by the Council of Europe?
2.What would Vinton Cerf, one of the father of the internet, agree as the key to dealing with cybercrime?Read carefully to fill in the blanks.Detailed readingStructurePart Ⅰ Para. 1
brief ____________ of cybercrime
Part Ⅱ Para. 2
____________of cybercrime
Part Ⅲ Para. 3-6
the situations and _________ of the problem
Part Ⅳ Para. 7-8
the __________ to the problemintroductionsolutioncategoriescauseslet's see if you can understand the text well Task-based reading
(Fill in the blanks)
(See your paper!)(para.1-2)The Internet has expanded lately, so h_____ the opportunities for crimes. Committing c_____ is realized online with little r____ of being caught. To fight this, we need to work together. The Council of Europe has c________ online crimes into four categories.
(para.3-4)Cybercrime has become s_____ today, and all Internet users are a_______ by it. Large companies are r____ targets for cybercriminals, who are often IT e_______. A survey c_________ in 2010 showed that almost all companies had their security system b______ into. Hundreds of billions of dollars has been lost to cybercriminals a________.
(para5-6)Cybercrime is so new that some governments have no laws a_____ it, and many holes e____ in their l_____ system. Most countries have no arrangements for dealing with s_______ of other countries who commit cybercrime, and they are difficult to c______.
(para7-8)Only by international cooperation can we s____ this problem. These criminals p_____ the best technical skills in the world, m______ that governments must combine their technological resources to keep ___. The UN is also required to form a special a_____ to act .
The Internet has expanded lately, so h___ the opportunities for crimes. Committing c_____ online is realized with little r____ of being caught. To fight this, we need to work together. The Council of Europe has c________ online crimes into four categories.para1-2 averimeisklassified(para.3-4)Cybercrime has become s_____ today, and all Internet users are a_______ by it. Large companies are r____ targets for cybercriminals, who are often IT e_______. A survey c_________ in 2010 showed that almost all companies had their security system b______ into. Hundreds of billions of dollars has been lost to cybercriminals a________.
(para5-6)Cybercrime is so new that some governments have no laws a_____ it, and many holes e____ in their l_____ system. Most countries have no arrangements for dealing with s_______ of other countries who commit cybercrime, and they are difficult to c______.
(para7-8)Only by international cooperation can we s____ this problem. These criminals p_____ the best technical skills in the world, m______ that governments must combine their technological resources to keep ___. The UN is also required to form a special a_____ to act .
Cybercrime has become s______ today, and all Internet users are a_______ by it. Large companies are r____ targets for cybercriminals, who are often IT e_______. A survey c_________ in 2010 showed that almost all companies had their security system b______ into. Hundreds of billions of dollars has been lost to cybercriminals a________. evereffectedipexpertsonductedrokennnuallypara3-4Cybercrime is so new that some governments have no laws a______ it, and many holes e ____ in their l_____ system. Most countries have no arrangements for dealing with s_______ of other countries who may have committed cybercrime, and they are difficult to c_____.gainstxistegal uspectsatch para5-6Only by international cooperation can we s____ this problem. These criminals p_____ the best technical skills in the world, m______ that governments must combine their technological resources to keep ____. The UN is also required to form a special a_____ to act. olveossesseaningupgencypara7-8conclusion1.what is cybercrime?
2.the categories of cybercrime
3.the situation and causes of cybercrime
4.the solution to cybercrime
Definition
What is cybercrime?
Cybercrime refers to any criminal offence related to the Internet. Reading strategy When we read some formal passages, we often come across some new terms or words. In order to help readers understand these difficult vocabularies and expressions , the author will give ___________of them in simple words.explanationsWhat is a definition?
How does a definition appear in the main body of a text?1. Usually it appears after the first use of the word in a phrase .
2. Occasionally it will appear in brackets after the word.
3. Normally it appears after a comma. 定义、解释或举例 通过 (is; was; mean; that is;
that’s to say; or; namely ;
in other words ; to put it
another way; i.e ; such as ;
like; especially; for instance;
for example ) 来确定词义常见的信号词真题演练(05 湖北卷A段)
Do you know what a “territory” is ?
A territory is an area that an animal ,
usually the male, claims(声称)as
its own. 根据定义,猜测词义领土,领域Practice makes perfect再试身手NEWS
1. Taiwan police declared that since August 2013, the cases of stealing telecommunication cost电信资费 by spreading mobile phones Trojan horse(using codes编码 to change the computer programme) occurred frequenftly in Taiwan.
2. Police say that in Huanan County, hacker ( someone who tries to break into computer systems, especially in order to get secret information)logged in 46 college websites, and forged the degree certificate伪造学历证书 to sell , suspected of fraud(activities done in a dishonest or illegal manner) crime.
We can retell the main idea in 30 words: With the development of Internet, various cybercrimes such as Trojan horse, hacker, fraud are finding their ways into people's life, causing a great loss to people .
Now it's your turn to tell the main idea of the text in about 30 words . _______________________________________________________________________________________________________________________________________________________________________________
(with the development of/ classify...into/ find one's way into people's life/ call for cooperation/ deal with...)Now it's your turn to tell the main idea of the text in about 30 words :
With the development of the Internet, cybercrime classified into four categories by the Council of Europe is finding its way into people's life, calling for people's cooperation to deal with it.---By netcitizens themselvesDiscussionDo you have any suggestions about how
to solve the problem of cybercrime?
How can you prevent yourself from being
cheated?---By government---By education书面表达:
随着因特网的发展与普及,网络犯罪已逐渐渗透到人们生活的方方面面。请针对这个问题用英语写一篇150词左右的短文。
1、 网络犯罪日益猖獗的原因(至少两点)。
2、如何打击网络犯罪现象?谈谈你的想法。
With the development and widespread of the Internet in recent years, cybercrime has also found its way into people’s everyday life. This is really worrying。HomeworkThank you !
Bye!
to
our class!By the end of the lesson, the students will be able to:know more about cybercrime
to master the reading skills of definition and skimming
to learn to summarize the text using the phrases learned in the text
12.9
On 12.9,1935 people went on street to call for a revolution against Japan to improve our life.Now we're again experiencing a revolution which changes our life a lot*Edward Snowden revealed the top-secret documents about the USA's surveillance programme.(监听项目)*Suzhou news said that Mobile Power Pack(手机移动充电宝) can steal customers' information while people are charging their mobile phone.Do you think it's legal or illegal?
we call this criminal offence related to the internet cybercrime.Have you ever experienced or heard about more examples about cybercrime?Group work Reading---let's know more about cybercrime.The fight against cybercrimeFast reading1.How many categories of cybercrime are listed by the Council of Europe?
2.What would Vinton Cerf, one of the father of the internet, agree as the key to dealing with cybercrime?Read carefully to fill in the blanks.Detailed readingStructurePart Ⅰ Para. 1
brief ____________ of cybercrime
Part Ⅱ Para. 2
____________of cybercrime
Part Ⅲ Para. 3-6
the situations and _________ of the problem
Part Ⅳ Para. 7-8
the __________ to the problemintroductionsolutioncategoriescauseslet's see if you can understand the text well Task-based reading
(Fill in the blanks)
(See your paper!)(para.1-2)The Internet has expanded lately, so h_____ the opportunities for crimes. Committing c_____ is realized online with little r____ of being caught. To fight this, we need to work together. The Council of Europe has c________ online crimes into four categories.
(para.3-4)Cybercrime has become s_____ today, and all Internet users are a_______ by it. Large companies are r____ targets for cybercriminals, who are often IT e_______. A survey c_________ in 2010 showed that almost all companies had their security system b______ into. Hundreds of billions of dollars has been lost to cybercriminals a________.
(para5-6)Cybercrime is so new that some governments have no laws a_____ it, and many holes e____ in their l_____ system. Most countries have no arrangements for dealing with s_______ of other countries who commit cybercrime, and they are difficult to c______.
(para7-8)Only by international cooperation can we s____ this problem. These criminals p_____ the best technical skills in the world, m______ that governments must combine their technological resources to keep ___. The UN is also required to form a special a_____ to act .
The Internet has expanded lately, so h___ the opportunities for crimes. Committing c_____ online is realized with little r____ of being caught. To fight this, we need to work together. The Council of Europe has c________ online crimes into four categories.para1-2 averimeisklassified(para.3-4)Cybercrime has become s_____ today, and all Internet users are a_______ by it. Large companies are r____ targets for cybercriminals, who are often IT e_______. A survey c_________ in 2010 showed that almost all companies had their security system b______ into. Hundreds of billions of dollars has been lost to cybercriminals a________.
(para5-6)Cybercrime is so new that some governments have no laws a_____ it, and many holes e____ in their l_____ system. Most countries have no arrangements for dealing with s_______ of other countries who commit cybercrime, and they are difficult to c______.
(para7-8)Only by international cooperation can we s____ this problem. These criminals p_____ the best technical skills in the world, m______ that governments must combine their technological resources to keep ___. The UN is also required to form a special a_____ to act .
Cybercrime has become s______ today, and all Internet users are a_______ by it. Large companies are r____ targets for cybercriminals, who are often IT e_______. A survey c_________ in 2010 showed that almost all companies had their security system b______ into. Hundreds of billions of dollars has been lost to cybercriminals a________. evereffectedipexpertsonductedrokennnuallypara3-4Cybercrime is so new that some governments have no laws a______ it, and many holes e ____ in their l_____ system. Most countries have no arrangements for dealing with s_______ of other countries who may have committed cybercrime, and they are difficult to c_____.gainstxistegal uspectsatch para5-6Only by international cooperation can we s____ this problem. These criminals p_____ the best technical skills in the world, m______ that governments must combine their technological resources to keep ____. The UN is also required to form a special a_____ to act. olveossesseaningupgencypara7-8conclusion1.what is cybercrime?
2.the categories of cybercrime
3.the situation and causes of cybercrime
4.the solution to cybercrime
Definition
What is cybercrime?
Cybercrime refers to any criminal offence related to the Internet. Reading strategy When we read some formal passages, we often come across some new terms or words. In order to help readers understand these difficult vocabularies and expressions , the author will give ___________of them in simple words.explanationsWhat is a definition?
How does a definition appear in the main body of a text?1. Usually it appears after the first use of the word in a phrase .
2. Occasionally it will appear in brackets after the word.
3. Normally it appears after a comma. 定义、解释或举例 通过 (is; was; mean; that is;
that’s to say; or; namely ;
in other words ; to put it
another way; i.e ; such as ;
like; especially; for instance;
for example ) 来确定词义常见的信号词真题演练(05 湖北卷A段)
Do you know what a “territory” is ?
A territory is an area that an animal ,
usually the male, claims(声称)as
its own. 根据定义,猜测词义领土,领域Practice makes perfect再试身手NEWS
1. Taiwan police declared that since August 2013, the cases of stealing telecommunication cost电信资费 by spreading mobile phones Trojan horse(using codes编码 to change the computer programme) occurred frequenftly in Taiwan.
2. Police say that in Huanan County, hacker ( someone who tries to break into computer systems, especially in order to get secret information)logged in 46 college websites, and forged the degree certificate伪造学历证书 to sell , suspected of fraud(activities done in a dishonest or illegal manner) crime.
We can retell the main idea in 30 words: With the development of Internet, various cybercrimes such as Trojan horse, hacker, fraud are finding their ways into people's life, causing a great loss to people .
Now it's your turn to tell the main idea of the text in about 30 words . _______________________________________________________________________________________________________________________________________________________________________________
(with the development of/ classify...into/ find one's way into people's life/ call for cooperation/ deal with...)Now it's your turn to tell the main idea of the text in about 30 words :
With the development of the Internet, cybercrime classified into four categories by the Council of Europe is finding its way into people's life, calling for people's cooperation to deal with it.---By netcitizens themselvesDiscussionDo you have any suggestions about how
to solve the problem of cybercrime?
How can you prevent yourself from being
cheated?---By government---By education书面表达:
随着因特网的发展与普及,网络犯罪已逐渐渗透到人们生活的方方面面。请针对这个问题用英语写一篇150词左右的短文。
1、 网络犯罪日益猖獗的原因(至少两点)。
2、如何打击网络犯罪现象?谈谈你的想法。
With the development and widespread of the Internet in recent years, cybercrime has also found its way into people’s everyday life. This is really worrying。HomeworkThank you !
Bye!
同课章节目录
- 模块9
- Unit 1 Other countries, other cultures
- Unit 2 Witnessing time
- Unit 3 The meaning of colou
- Unit 4 Behind beliefs
- 模块10
- unit 1 building the future
- unit 2 people on the move
- unit 3 protecting ourselves
- unit 4 law and orde
- 模块11
- unit 1 careers and skills
- unit 2 getting a job
- unit 3 the secret of success
- unit 4 the next step